How to sign git commits with Yubikey
Introduction
If you know what a Yubikey is, you may skip this section.
Yubikey is quite expensive device that acts as a portable GPG key, it is considered secure because once the private GPG key is on the device, it can’t be extracted again (unless someone finds a way).
You can import your own generated GPG keys or generate a new key-pair directly on Yubikey.
Yubikey can do a lot more than holding a GPG key, It can do two-factor authentications with sites like Google, Github or Dropbox. The list of all supported sites are available on their official website. You can also use them with your mobile phone, if you have NFC, when you login to Google using your credentials, if NFC is on, the phone asks you to put the Yubikey on the NFC sensor so it can communicate with it, if you don’t have NFC the website will fall back to another two-step authentication method that you have enabled for your account.
You can also use Yubikey to login to remote ssh machines or to login on your laptop, but that’s a bit risky, if you have only one key, because if you lose the key, you are locket out of your own devices and servers unless you have a second backup Yubikey.
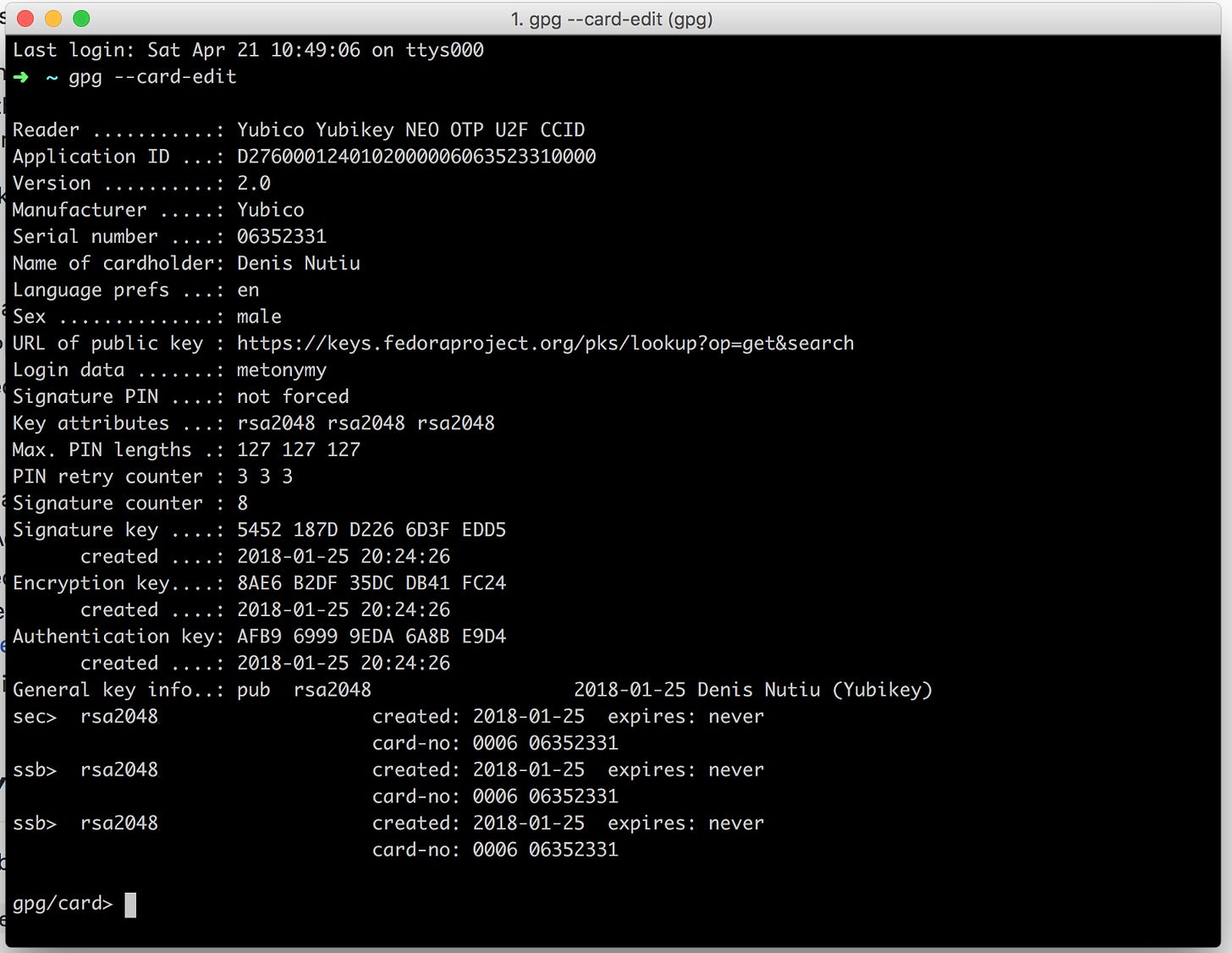
You can pretty much personalize your Yubikey using gpg --card-edit when your Yubikey is plugged in. Here’s the output of the command on my machine:
Singing git commits
If you want to have a fancy badged saying “Verified” next to your commit then follow these steps:
Generate your GPG key-pair on Yubikey. Run:
gpg --card-editand thenadminto allow admin commands. See if you can find the right command usinghelpin order to generate your keys.Go to Github->Settings->Security and add your public key there.
Configure the signing key.
https://git-scm.com/book/en/v2/Git-Tools-Signing-Your-Work 4. Verify your commits when committing with the -S flag. If you already have a commit you can type: git commit --amend -S --no-edit in order to verify it.
Push the commit.
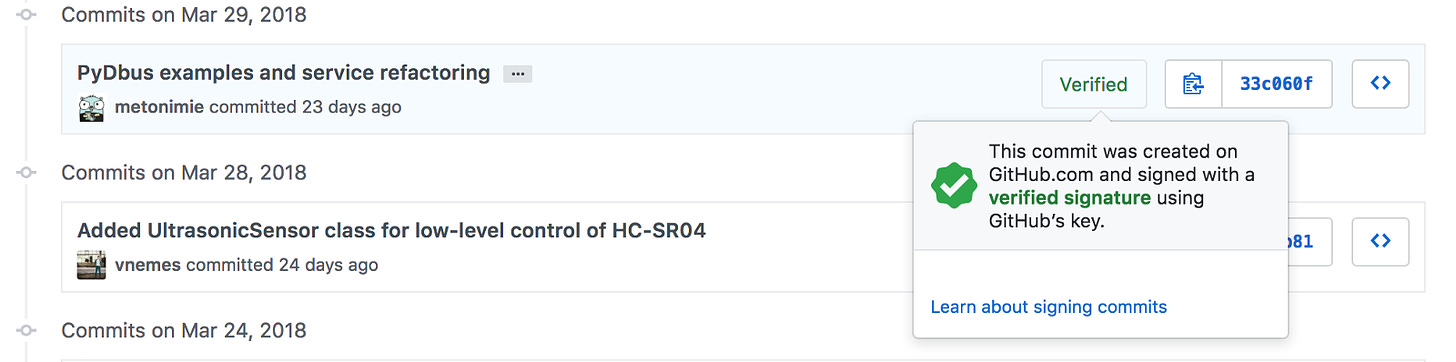
The “Verified” badge will prove, that you and only YOU have made the commit and if someone hijacks your github account and tries to push a malicious commit, they can do that but they can’t verify the commit, thus, if you’re working on a high-security project, you and your team may have set some rules that every commit must be verified with a personal GPG key.
If you like what I’m blogging about, you may follow me on Twitter



